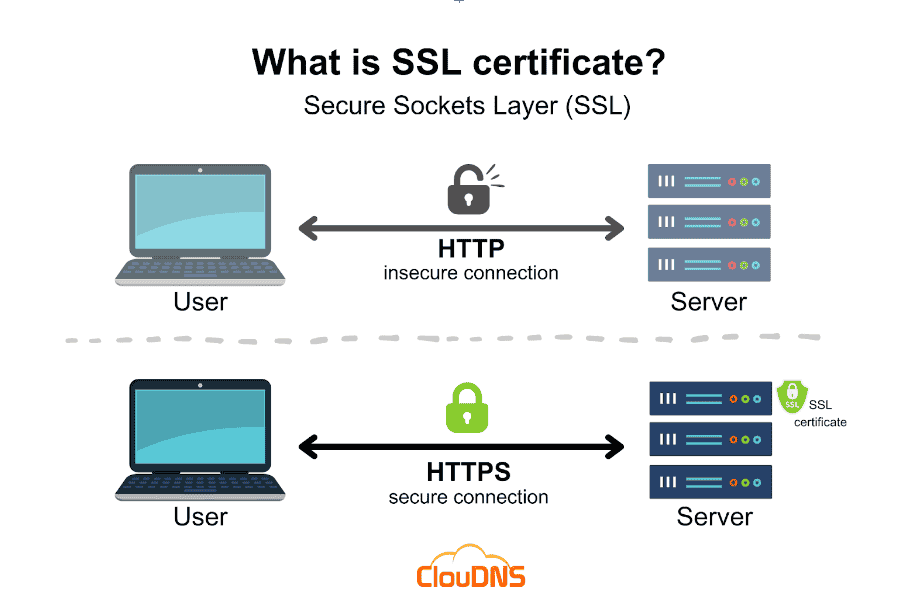
If you ever worked on any type of website, you’ve heard you should implement SSL encryption. Furthermore, even if you only browsed the internet, you’ve been likely notified if you’ve ever tried to open a website without an SSL certificate.
When browsing the Internet or developing websites, security must always be considered. Even if cybersecurity isn’t your main interest, it’s essential to implement some concepts into your code.
Suppose you don’t want your users to become one of hundreds of millions of cybercrime victims, you should pay close attention to cybersecurity and understand methods such as SSL/TLS inspection to protect your website.
Breakdown of SSL/TLS
SSL, or Secure Socket Layer, is a cryptographic protocol introduced in 1995 to provide better security for data in transit. This has significantly improved, as sensitive data transferred between a server and a client is now protected.
However, only after a few years was the SSL protocol replaced by the Transport Layer Security protocol, which served the same purpose yet had many upgrades. SSL was vulnerable to various attacks, one of the most popular ones being the POODLE attack.
A couple of years after the introduction of the SSL protocol, TLS emerged and quickly replaced it. What’s interesting is that people still colloquially call the TLS protocol SSL.
TLS is an essential protocol that makes many everyday internet activities safe and meaningful. It protects against eavesdropping, forgery, and tampering while protecting sensitive data such as passwords and financial information.
A brief history of SSL & TLS protocols:
- 1995: The first version of an SSL protocol emerges
- 1995: SSL 2.0, which led to some improvements
- 1996: The final version of the SSL protocol was published, SSL 3.0, which was still highly vulnerable
- 1999: TLS 1.0 emerges as a replacement for SSL 3.0
- 2006: After more than 6 years, TLS 1.1 was published, showing just how relevant and secure this protocol has been compared to SSL.
- Lastly, TLS 1.2 and TLS 1.3 were published in 2008 and 2018, respectively.
TLS versions 1.2 and 1.3 are the only versions of all the mentioned ones that are in use and aren’t deprecated. Although some websites still use outdated protocols such as SSL or TLS 1.0, it’s highly advisable to configure and disable your server.
The process of establishing a secure connection between a client and a server has five steps:
- The client, you, and the user send a request to the server, including supported cryptographic algorithms.
- Then, the contacted server responds with a set of algorithms and its SSL/TLS certificate.
- Both parties exchange certificates and verify each other’s authenticity.
- The parties exchange a session key that’s used for encrypting data
- The communication is now encrypted using the session key previously agreed upon.
SSL/TLS inspection is a critical component of secure web access, allowing security teams to decrypt, analyze, and re-encrypt encrypted traffic for potential threats. This capability is essential for detecting and preventing sophisticated attacks that may hide within encrypted connections.
By implementing SSL/TLS inspection, security professionals can gain visibility into encrypted traffic, identify malicious activities, and respond to threats more effectively. This aligns with best practices for defense-in-depth strategies, which often incorporate the MITRE ATT&CK framework to understand and mitigate various attack techniques across the cyber kill chain.
Fake versions of websites used for phishing usually don’t have security certificates. Google penalizes websites without a certificate to lower users' chances of visiting them.
What’s SSL/TLS Inspection

Just like SSL and older versions of TLS became obsolete at one point, there’s a lot more to cybersecurity than data encryption. Hackers adapted to these protocols and leveraged encrypted traffic to conduct malicious attacks.
Cybercriminals use encryption to hide different types of attacks. Even with TLS 1.3, a hacker can still infect your server with malware and conduct phishing or brute-force attacks.
SSL/TLS inspection is a cybersecurity method that decrypts encrypted internet traffic to examine it for threats and then encrypts it again before it reaches its destination. However, traditional cyber attacks aren’t the only problem you should worry about.
Another term for SSL/TLS inspection is deep packet inspection, so avoid any confusion if these two terms are mentioned interchangeably.
Hackers continuously invent new attack methods, the so-called zero-day threats. These threats are new, and SSL/TLS inspection can help identify them and identify suspicious patterns before they damage your systems.
When conducting this, you need to incorporate both inbound and outbound inspection. The inbound traffic flows toward the client and the outbound traffic flows toward the server. You need to implement inbound inspection through intrusion detection systems.
Benefits of an SSL/TLS Inspection
There are general benefits that all cybersecurity solutions can help you. But, there are also specific threats and security benefits that SSL/TLS encryption brings you. By inspecting encrypted traffic, you’ll increase your chances of recognizing and stopping cyber threats.
This helps your company prevent unauthorized access or even larger problems, such as data loss. With various data regulations in place, preventing data loss is essential to avoid fines and reputational blows.
In short, SSL/TLS can help your company comply more with relevant data regulations such as GDPR and CCPA.
SSL/TLS inspection can also lead to other actions, such as content and URL filtering, providing your company with a way of restricting access to harmful web pages or malicious content.
In the future, SSL/TLS inspection can become even more popular and efficient. For example, you’ll be able to leverage the latest trends, such as machine learning and AI, to recognize malicious patterns quickly.
Furthermore, Cloud Workload Protection Platforms (CWPP) enhance SSL/TLS inspection for secure web access by decrypting and inspecting encrypted traffic to detect hidden threats. They provide visibility into encrypted communications, enforce security policies, and automate SSL/TLS certificate management.
By integrating these capabilities, CWPPs ensure robust protection for cloud workloads, preventing encrypted traffic from becoming a blind spot for cyber threats while maintaining performance and scalability.
Why is SSL Inspection Needed?
A simple explanation of why an SSL/TLS inspection is needed is that most threats are encrypted nowadays. Other websites can also obtain hundreds of SSL certificates, allowing anyone to create a malicious website.
This is dangerous for individuals who leave their sensitive data on such websites. However, this is also an internal problem for companies. For example, your employees might leave vulnerable data in the wrong place, which can be leveraged for insider threat attacks.
URL filtering, mentioned earlier, could be a solution for this. Regardless of what other cybersecurity protocols you implement, you can best observe some threats through an SSL inspection.
Securing data in transit through SSL inspection isn’t the only thing companies should have in place. They should also protect this stored data. It’s important to factor both costs into the security structure of your website.
When budgeting for security, businesses need to factor in both real-time security measures (such as SSL inspection tools) and long-term data storage protection costs (like AWS Backup).
This is where AWS backup costs can become an important part of the conversation, as the cost of securing stored data should be planned alongside the cost of SSL inspection.
However, not all websites and companies conduct SSL/TLS inspections, as this requires a lot of resources. Some companies don’t have the necessary computing power and employees to perform them.
You can solve this by either committing to creating a solid security framework with proper devices and experts or outsourcing SSL inspection to third-party companies that specialize in this.
Risks Associated with SSL Inspection
Of course, there are some potential risks that you should be wary of when conducting an SSL inspection. Mainly, you’re decrypting traffic that can be sensitive and personal, which raises a privacy concern.
Depending on the regulations and privacy laws that apply to your company, an SSL/TLS inspection can be seen as a privacy intrusion. You must ensure that if you conduct this, you adhere to all the necessary regulations and frameworks.
Encrypting and decrypting data can also lead to vulnerabilities, so it’s essential to prevent potential data leaks and Man-in-the-Middle attacks while conducting the inspection.
As mentioned, an SSL inspection can require a lot of resources, which can lead to downsides in terms of user experience and service availability at the end-point.
Conclusion
More or less, all cybersecurity measures and protocols can significantly improve your company’s or application’s defenses. However, none of them can guarantee 100% protection against cyber threats.
You should always strive to incorporate effective methods that have stood the test of time and that can protect your weak points. Not all companies need all cybersecurity protocols and processes.
You should conduct regular audits to determine which methods yield the best results with the least resources.
Author:
Jeremy is co-founder & CEO at uSERP, a digital PR and SEO agency working with brands like Monday, ActiveCampaign, Hotjar, and more. He also buys and builds SaaS companies like Wordable.io and writes for publications like Entrepreneur and Search Engine Journal.